The Task Force was briefed by a wide variety of officials and members of the Defense and Intelligence Communities. Several consistent themes became apparent. The "Changed World" in which we live, the changes in threats to the United States, the impact of the "Peace Dividend," and our concomitant expanded "global vision" all drive us to realize that information, per se, has become a precious commodity to the U.S. Further, our existing intelligence structure, collection, analytic and information integration capabilities are optimized for yesteryear. Even though we clearly need specific intelligence collection in a number of areas, such as from networked systems such as the INTERNET and other open sources, it became readily apparent that we do not effectively exploit all of the data that we already collect! The decrements, often horizontal, in analytic resources increase the need for effective integration of the analysis processes across the Intelligence Community (IC). Neither our current structure nor our information processing systems are optimized for the new world set of problems.
Issues relating to Intelligence Community resources, IC support to the military acquisition processes, strengthened IC Issue Managers, review of intelligence collection investment strategies, and developing areas of IC business excellence, all point to a critical need for improved intelligence information integration. We simply will not return to the larger number of analytic resources of the cold war; thus a new paradigm is urgently needed. A "New Vision" is proposed.
The Director of Central Intelligence, in concert with the Secretary of Defense, should create "A New Vision" for intelligence exploitation in the U.S. This "New Vision" would lead to the mission of an integrated National Intelligence Exploitation Architecture which, over time, would develop the meta core system (integrated system of systems) for the National Intelligence Community.
Why do we need this New Vision? Because our existing exploitation and analytic systems were created and built during a period in which virtually all such systems were custom designed and implemented; and thus "stove piped" for specific tasks without particular regard for interfaces and compatibility with other systems. These existing systems were built for what became relatively well understood problem sets with characteristics such as:
In relative terms, this was a fairly static target set for many years.
Our world has changed to the extent that we now do not know who all of our potential adversaries are, or might be. Who would have predicted two years ago that Rwanda, Somalia and Haiti would demand so much from our intelligence communities. Our requirements now are for globally based intelligence, dynamic in nature and rich in detail, which include increased exploitation of open sources and networks in a totally new information age. The INTERNET provides potential for access to rich repositories of open source information. However, IC access to the INTERNET raises difficult questions and serious concerns about conflicts between law enforcement, intelligence activities and constitutional guarantees. These issues will have to be addressed as part of the NIEA.
Given this shift, we should not be surprised that our existing exploitation and analyses systems do not provide the level of capability required in the new world in which we live.
It is estimated that the National Intelligence Community invests between one and two billion dollars a year in new information management technology (not signal processing, although substantial sums are invested there as well). Additionally, DARPA has over $300 million in its budget for advanced computational technologies alone.
If we focused one-quarter of these moneys towards a coherent, integrated and distributed exploitation and analysis system(s), the U.S. could invest the necessary resources to realize this architecture over the next decade. Why would we wish to do so?
First, our dramatically changed world has been exacerbated by our "Peace Dividend" in the sense that we have taken substantial billet reductions in analytic resources. Thus, we can no longer afford the redundancies of the past and at the same time, we must be able to adapt our exploitation and analysis by sharing (or in many cases shifting) the analytic processes in real- time.
Second, hardware and software technology permit us now to design and implement relatively open systems that have a high degree of interoperability and can use a great deal of COTS. We no longer require the vast majority of our systems to be custom and monolithic! We can have systems that can be modified quickly to address changing requirements and to take maximum advantage of rapidly developing technologies.
Third, the NFIP is going to spend (has budgeted) a larger amount on information technology per year, but in a largely diffused manner. Today, there is neither a coherent architecture, nor focused activity to distribute our development activities in such a way to bring together the best IT resources of the entire Intelligence Community into a highly distributed and interoperable meta system. Surely there are some excellent IT development activities occurring in the IC. These should continue, but in the broader framework of where we need to be in the 21st century. If the past ten years are an example and absent a coordinated development activity as proposed here, we will spend billions of dollars on information technology in the NFIP alone without achieving the kind of integrated capabilities we must have for the 21st century.
How would this work? The "New Vision" would drive the creation of an architecture, supported by enforced building codes (standards, interfaces, security protocols, etc.) in which development activities would be parsed to specific agencies of the IC and supported by the experience of, for example, DoD's experience in promoting interoperability in the JROC process and the development of the GCCS. Over time, each agency would become a center of excellence for a particular area of technology. All of this would fit within the framework of the architecture to permit modules of capability to be developed by one agency for the benefit of any or all other agencies. Let's take but a few examples:
In each of these cases, there would be strong emphasis on exploiting and integrating technology from the private sector as well. For example, Time-Warner and Salomon Brothers are but two firms investing hundreds of millions of dollars in advanced information technology. We need to assess where the private sector will be providing the research and development so as to leverage those developments and conserve our scarce resources for R&D specific to IC/DoD needs and for integration of commercial technologies.
Over time, the IC could develop a series of interoperable systems which would be less expensive and more powerful by several orders of magnitude for the 21st century, than if we proceed during the next decade in the same mode as the last decade.
The Intelligence Community will have to change in response to the NIEA. Carrying out the initiative may require a more highly centralized focus on information systems that are both within individual organizations and across the IC as a whole. Long-debated plans for Central Information Services Offices may have to be implemented to create the budgetary resources and organizational authority needed to guide an internal information revolution. A Central Information Council may be needed at the SECDEF/DCI level (perhaps to include other government agencies) to establish policy and to guide the IC to focus on common interests. Whatever organizational reforms are taken to ensure the success of the initiative, change will be needed to break down resistance to change, shift established patterns of investment, and enforce a high degree of cooperation and interoperability.
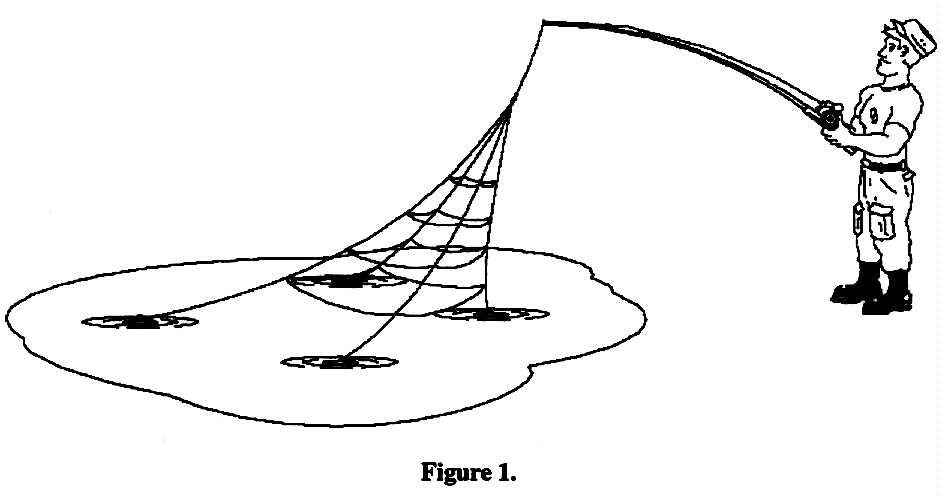
The most difficult part is to make the decision. To commit to a road map of information technology which will become the exploitation and analysis meta system (or system of systems) of the 21st century. The target environment is an integrated, yet highly distributed, heterogeneous IT infrastructure which -- over time -- will permit an individual in the Intelligence or Defense Communities to query this information environment (much as can be done today on INTERNET). The responses would be relevance ranked and presented in a contextual framework pertinent to that particular user. Thus, military commanders/CINCs, acquisition managers, intelligence analysts and a myriad of other users could gain access to the most comprehensive and broadly based information and intelligence available. Sure security is both an issue and a potential problem. Keep in mind that we are talking about the system for the 21st century and many of the security issues of today will be resolved either procedurally (a la the Joint Security Commission Report) or technically through protective hardware and software. Figure 1 illustrates the concept whereby an individual seeking information "goes fishing in the sea of data." The system would understand some of the context from which the query was made. and as the user asked additional and clarifying questions, the system builds more and more relationships pertinent to the user's needs. Additionally, the system is capable of making queries by example. Thus, the user could ask, "tell me if you know of any more of those." Alerting tools would be embedded in this as well. Both AT&T and American Express have profiles of millions of users which, when violated or exceeded, alert the service provider of anomalies in spending, geography or activity norms. Some of these norms are dynamically adjusted automatically as people use their phone or credit cards.
What the User NeedsAn easy capability to extract information related to his problem from the mass of data (national and otherwise) available on distributed problem solving networks

Figure 2 illustrates the distributed nature of the component systems. They could be spread across Washington, the country, or the world. The key is that, like the INTERNET, the user does not have to know where information is stored in order to retrieve it! His query will seek data through the network of servers/routers/switches that dynamically interface the systems. Although today's INTELINK is a significant improvement over a couple of years ago in accessing intelligence from remote, distributed agencies and commands, it relies on pre-identified and indexed intelligence. What we need for the future is a system that aids the user in finding "unknown" information.
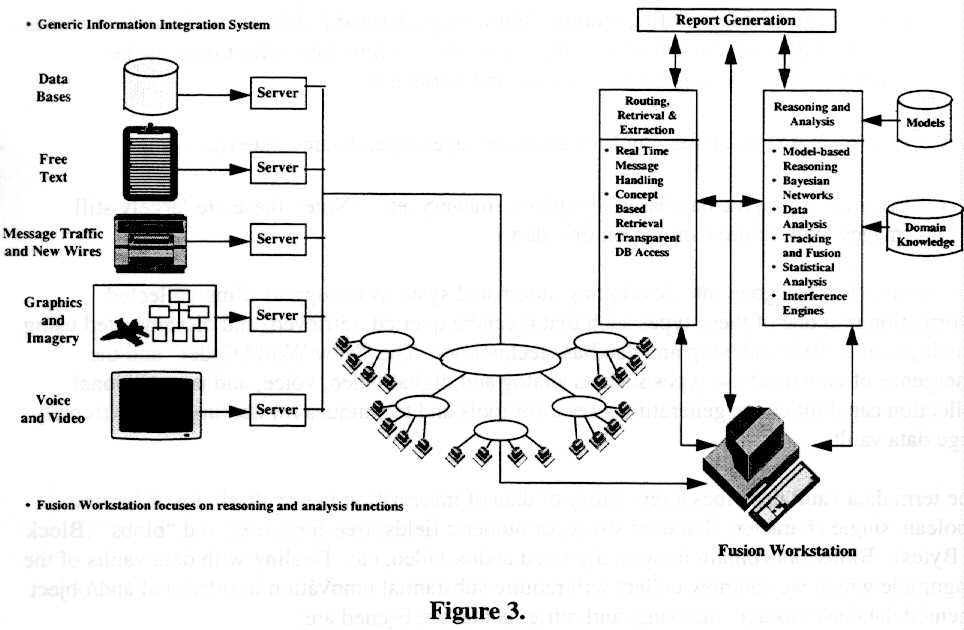
Figure 3 shows how an integrated interactive multi-media workstation would have (or access) decision aids, correlation and fusion aids and visualization tools to provide the user the most pertinent and timely information. There is no intent to create and keep current monolithic data bases from which searches would be made. Data bases, as we currently know them, are necessary but hardly sufficient for our 21st century purposes. More about that shortly.
A powerful aspect of this proposed National Intelligence Exploitation Architecture is that this identical infrastructure could support all of DoD, or all of the government. The tools, techniques, technology and integration required to build and implement this system, need only to provide access to the data sources others might need to serve all of DoD or all of Government. Surely there would be requirements for domain specific tools, decision aids and presentation unique or nearly unique to particular user communities. But the underlying infrastructure would be as widely applicable and robust for all, as is the INTERNET today and tomorrow. There is within the DoD a Common Operating Environment (COE), used principally as the core of the GCCS and some other C2 systems. This may offer a starting point -- a building block -- from which design the NEA.
Surely many of the issues associated with the successful implementation of this architecture seem intractable today. A great deal of technology R&D and technical development must be accomplished and integrated over time to achieve these goals. This is a journey we believe is absolutely essential. Our existing "stovepipe" systems were built with old technologies under different paradigms. We have a new world, and a new paradigm for sharing information -- most of which will now be unformatted, in contrast to most information in existing intelligence data bases.
Most of the existing analytical support systems in use today deal with three major types of information in various storage sizes (e.g., megabytes to terabytes). The information types are:
Enormous effort has gone into developing automated systems to support filing collected information into one of these types such that it can be queried, retrieved, and disseminated using existing (circa 1980) indexing and database technology. The "New World Order" and the emergence of new database types such as analog and digital video, voice, and new National collection capabilities are generating a need for tools and techniques for dealing with extremely large data vaults.
The term data vault describes a repository of data of information in a multiplicity of formats Boolean, single character, character string, or numeric fields; free-form text; and "blobs" (Block of Bytes). Blobs can contain images, digitized audio, video, etc. Dealing with data vaults of the magnitude which we can now collect will require substantial innovation in relational and/object oriented database storage, indexing, and retrieval that are needed are:
There are a number of systems under development which may attack some of these issues. For example, EOSDIS will collect, store and make accessible on the order of terabytes a day.
Refer back to Figure l which illustrates the capability needed for the user in response to the explosion of dissimilar information to which we have and need access and understanding. The technologies cited above can be referred to as those necessary to provide Distributed Problem Solving (DPS) capabilities to intelligence analysts and others.
While we attempt to attack the multi-source correlation and fusion problem with the automation, we often overlook the finest and fastest correlation system available - the human eye, ear, and brain. Further, almost since the beginning of application of ADP technology to intelligence problems, analysts have asked for a "smart map."
The third fundamental piece of the puzzle is finding ways of displaying complex and voluminous disparate data streams such that our premier correlation tool can visualize them. A true smart map is one presentation approach, to which almost any analyst can relate. Some of the features included in smart maps would be: pan and zoom, movable viewpoints, active regions, alerts and alarms, validity representation and so on.
In addition to these smart map capabilities, we need better ways to visualize dynamic phenomena such as occurrences of scenario events with respect to time, and to integrate temporal and spatial relationships in displays, operations clocks, etc. These need to be integrated with the smart map display, with corresponding active regions on the timeline displays such that the analyst can access the same information from either place. Display techniques are needed to allow visualization of problems with dimensionalities higher than four (three-space + time).
Additionally, efforts in voice recognition technology could minimize keyboard entry of database and knowledge base input and queries.
The technologies cited above (and a number of others such as imagery processing, compression techniques, interactive multi-media, etc.) represent a panoply of capabilities, some of which are far more attainable or cost effective than others. Some are more likely at the end of a decade, others reasonably soon. Much of the needed technology is being developed, or will be developed in the private sector. Systems for voice recognition and understanding are already replacing commercial telephone operators; office work stations are already taking dictation; personal computers are translating scientific journals from Japanese into English. Image understanding systems are being used to read x-ray mammograms and inspecting cell cultures. Advanced computer systems are being used by commercial airlines for resource allocation and logistics planning beyond human capabilities. Other applicable commercial developments include worldwide, point-to-point voice, compressed data, and even encrypted communications for cellular phones and the INTERNET. The entertainment industry is investing huge sums to develop new wideband data distribution systems (i.e., high definition television) and direct, digital broadcast satellites.) These are all technologies which are directly applicable and will be developed far faster by commercial industry than by the government.
These technologies need not be developed twice. The trick, or course, is to pick the right ones; fit them into a critical path, and integrate them into the National Intelligence Exploitation Architecture. This drives us to realize that integration, per se, is becoming and must become a technology in its own right. Advanced integration tools, techniques and testing require significant development. DARPA, in concert with the private sector, is the obvious candidate to tackle these issues.
The challenge then for the Intelligence Community (the DCI and SECDEF) is to:
It is believed that adequate funds are present in existing NFIP (with partial DARPA support) budgets to support this architecture. Success would take commitment to a coherent road map and parsing varied development activities to agencies which would essentially become centers of excellence for varied components of this architecture. This program provides the framework for our 21st century intelligence exploitation and analysis support to government.