
This appendix provides background information on issues and recommendations developed by the Technology Panel of the Task Force. It is provided for reference and further discussion of the issues and recommendations contained in the basic report. Technology recommendations made by the full Task Force are included in the basic report.

Issues developed by the Technology Panel are presented in a set of key technology areas for Information Warfare Defense, which are grouped as shown.

Current system vulnerabilities are due in part to lack of attention to security and survivability issues during design and development of computing and communicating technologies. Now that the collective vulnerability due to dependence on these technologies is recognized, it is equally important to recognize the need to address security and survivability concerns in the development of new technologies. Security and survivability must be treated as critical requirements in the conceptualization and development of new and emerging technologies. While new technology is in its earliest conceptual stages, there are unique opportunities to influence developments so as to minimize vulnerabilities and strengthen security.
Information security needs to be incorporated early on in new information systems technology development. It is essential that the government and commercial developers of products for information systems cooperate in the evolution of common standards for robust products and practices. Information security and survivability should be incorporated early on in the development of new information systems. It is recommended that significant attention be given to stimulating and encouraging this process. Areas where commonality of robustness standards and practices should be pursued include: component hardware and software products; security interfaces; system management policies, procedures, and processes addressing such issues as compliance assurance, configuration management, administrative oversight, and robust systems operational training programs.
Since a significant level of research in the information technology area is funded by the DoD, security and survivability should become required aspects of funded programs. In addition, a DoD funded research activity should be directed at vulnerability- and countermeasures-oriented analyses of new ideas and emerging technologies, and making the results widely available to the research community.


COTS INFORMATION SYSTEM TECHNOLOGY EVALUATION CAPABILITY
Economic pressures are driving the DoD toward use of COTS information systems technology, rather than custom mil-spec systems. Unfortunately manufacturers are not motivated to develop defensive IW features in their products, since commercial customers generally are not demanding them, and such features typically impact performance. Thus the DoD must take special measures to insure that the COTS approach provides adequate DIW protection for DoD applications. It is recommended that a COTS information system technology evaluation capability be established within the DoD, in order to characterize vulnerabilities in COTS products, and to develop means for dealing with their deficiencies. Basic DIW performance/certification criteria should be developed, focusing initially on DoD needs but conforming to best commercial practices insofar as possible. A major long term goal is to foster collaboration with the commercial marketplace, and plans should be developed to migrate toward a national joint DoD/commercial technology evaluation capability, rather than unilaterally setting rigid DoD requirements that ultimately will be resisted or ignored by industry. This organization or set of organizations should identify product vulnerabilities, discover workarounds, and disseminate the results. The idea is to understand the risks and learn to operate in the face of them. Currently many DoD organizations would have to analyze these products themselves; a central facility would leverage scarce expertise and save money. Such a center could serve a role like a "Consumer's Union," and informal rankings of products could be provided, which could act as a spur to vendors to improve their products.
R&D is needed, preferably with joint government/industry support and working with both the offensive and defensive IW communities, to develop means for identifying product vulnerabilities to both established and emerging threats, disseminating information on such weaknesses, and developing corrective measures. Such a technology evaluation center should also provide risk assessment/advisory services to system developers and users, perhaps based on the current Internet model of cooperation.
Note - Implementation of this recommendation is not trivial. The intent is to develop the capability, which will undoubtedly need to be tailored for different products. The tailoring/application of the capability should be distributed. One possibility is to require that before a COTS product is incorporated into a DoD system,, the capability must have been applied. Program offices could take results from previous application of the capability or pay for its application. The expectation is that this will create a market incentive for vendors to submit (and even pay for) their system for test. The funding proposed is only for development of the capability.

MATURITY MODELS
The trend toward increased use of commercial off-the-shelf software, open systems and wide area networks, is placing the information assets of many organizations at risk. These organizations may not be aware of the risks associated with these new environments, and may not be aware of the key engineering and network management practices that can be used to mitigate the risks. Acquisition and engineering managers lack comprehensive models and analytic techniques to evaluate the impact of architectural and other design choices on system robustness before major implementation investments have been made. Once networked systems are placed into operation, network operators often depend on practices and tools that were developed to assure the integrity of proprietary networks that had limited external connectivity and that were based on custom-designed software. Integrity assurance techniques developed for these restricted environments are not adequate for open, wide area networks or for an environment characterized by rapidly changing technologies and threats, and are typically focused on classical security issues.
Organizations that acquire and operate networked systems are in need of models, guidelines and tools that are effective at helping them acquire and operate systems that are highly resistant to attack, that are able to limit the damage from successful attacks, and that are capable of rapid recovery from attack. As missions, technology and threats evolve, these organizations also need system robustness assessment methods that allow them to adapt to the changing environment. Models, methods, and tools should be developed and refined concurrently to insure that management practices are aligned with the technology that supports them. The areas indicated below should he addressed
Robustness Engineering Models
It is recommended that existing Software and Systems Engineering Capability Maturity Models be extended to describe the key engineering practices and technologies needed to allow organizations to specify and analyze non-functional attributes, such as security, as the system architecture and implementation design develops. The models should provide guidance on the process of analyzing robustness attributes, and making engineering tradeoffs. The models should be validated through empirical tests that demonstrate their ability to reflect the desired robustness attributes of the delivered systems.
Robust Systems Acquisition Maturity Model
It is recommended that the existing acquisition maturity model be extended to provide descriptions of the key practices acquisition organizations should follow to improve the robustness (including security) of acquired systems. This model should insure that the acquisition process specifies and monitors the use of robust system engineering practices for custom software, and specifies the use of robustness evaluation for off-the-shelf software.
Survivable Network Management Model
While it is unrealistic to expect that robust survivable systems can be achieved only through good management practices, it is widely recognized that without good management practices it will not be possible to secure critical systems against information warfare attacks. There is a need to develop and adhere to standardized policies, procedures and practices for management of information systems. Management and validation of information systems must be given the same priority as that given to achieving and maintaining readiness of weapons systems. It is recommended that a model be developed that provides a description of the key practices an organization should have in place to improve the robustness and survivability of its installed, networked information systems. The model should be structured as a set of key practices where each practice definition contains: (1) a description of the key practice; (2) a rationale for implementing the process; (3) guidance on how to implement the practices that helps organizations balance the value of the assets being protected with the costs of various forms of implementing the practice, the effectiveness of each form or practice, and the magnitude of the threat
But more than a Network Management Model is needed. Automated tools are needed which will allow integrated management of large, complex, heterogeneous networks, with automated enforcement of an organization's survivability and security management models.
Robustness Assessment Methods
It is recommended that robustness assessment methods be designed to allow an organization, with minimal outside expertise, to analyze its practices against each of the system robustness models for the purpose of identifying its current state and developing robustness/survivability improvement strategies and plans. The assessment methods must:
- be suitable for self-assessment;- yield detailed results that tell an organization where it is, where it should be, and how to get there;
- take advantage of a knowledge base that tracks threats and vulnerabilities; and
- be self-tailoring to the organization being assessed.
Robustness Improvement Toolkits
It is recommended that robustness improvement toolkits be developed that provide the tools needed to support the assessment methods and the key practices defined by the models. Tools must be structured to encapsulate knowledge of system robustness practices to leverage scarce human resources in order to help people understand which tools to use for what purposes, and promote commercialization of the tools and a community of vendors to extend and maintain them over time.
As these models and practices evolve, it is recommended that they be applied to and evaluated for effectiveness against critical elements of the national, information-dependent infrastructure, such as energy distribution, telecommunications, and transportation systems.

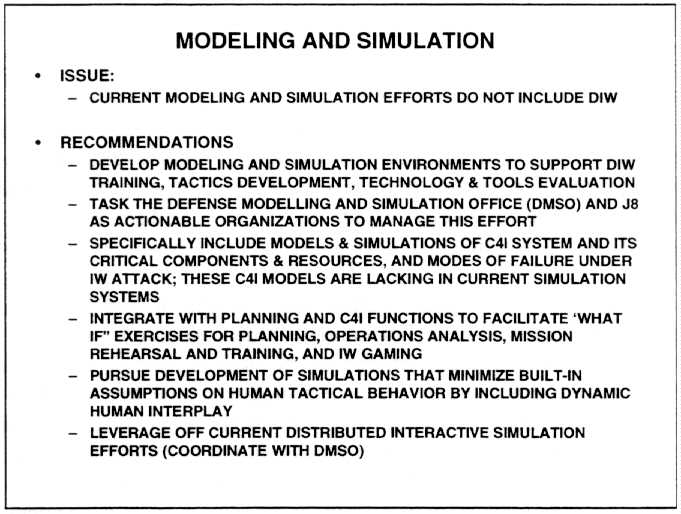

RED TEAMING
Red Teaming is an essential component of the DIW strategy and technology development process, but it is recommended that the concept be extended to include vulnerability analyses as well as carefully planned attacks during experimental activities in controlled testbeds and during training/planning exercises. The Red Team exercises should be conducted under proper rules of engagement to avoid unnecessary damage or disruption to information systems. The vulnerability analyses should be utilized by an Anti-Red Team to perform robustness engineering and to plan for fighting the Information War during the exercises as well as during operations.
Emphasis should be given to developing new attack methodologies in addition to reuse and application of current attacker techniques. For example, attacks should be designed which exploit the system's survivability features, which must be assumed known to a sophisticated attacker. In formulating these attack strategies, models should first be developed for system vulnerability and its likely defenses, and these models should be exploited in the attack strategies. Vulnerability analyses and Red Team attacks should be conducted at the application and system level, as well as at the subsystem level, with the goal of uncovering how operations can be perturbed (e.g., the planning and execution of an air tasking order or the deployment of sensors and communication assets), and how supporting communication links, or specific computers and network nodes can be compromised.
In addition to Red Teams, it is recommended that Anti-Red Teams (DIW Teams) be formed and tasked to prepare for and fight Red Team attacks. These activities will provide the basis for developing strategies and tools for use during operations to detect and respond to Information Warfare attacks. The Anti-Red Team should also be charged with providing inputs to the system designers and builders to assure the incorporation of robustness features. Network managers should be included as part of the DIW teams to assure that damage containment and service restoral techniques are effectively exercised as part of the counter-IW operation.
COORDINATION AMONG OFFENSIVE IW, DEFENSIVE IW, AND INTELLIGENCE
In any adversarial situation, the offensive side enjoys an inherent advantage over the defensive side, since they own the initiative, and need discover and exploit only one flaw in a defensive perimeter to achieve their ends. In contrast, the defensive side must attempt to foresee and protect against every conceivable form of assault. The situation prevails in the IW context, and it is clear that the defensive side would greatly benefit in developing risk management strategies and protective mechanisms from an awareness of the offensive side's view of the vulnerability profile and preferred set of attack techniques and approaches. The friendly offensive IW team would also benefit by interplay with its DIW allies, which would enable the offense to hone its tactics and techniques and anticipate potential counter-IW tactics. In addition, intelligence units should work together with both offense and defense to increase overall effectiveness of IW and to avoid unnecessary vulnerabilities.
It is recommended that a mechanism and a forum be developed to support a continuing, dynamic dialogue and interplay among the offensive, defensive, and intelligence communities. This activity should include information exchange on new vulnerability discoveries and attack techniques on the one hand, and red team vulnerability assessments of emerging defensive techniques and technologies on the other hand.
To provide an objective mechanism for facilitating and coordinating this dynamic interplay, an independent "ORANGE" team could be formed, devoid of vested interests on either the offensive, defensive, or intelligence sides. The orange team can also play the role of umpire and objective score keeper in red-team/vulnerability assessment war gaming activities. In general this type of 3-way interaction will lead to a better understanding of the fundamental exploitable flaws typically occurring in system and communication software, distributed system architecture, communications infrastructure, and system management policies and procedures. This will also lead to new tools to address these particular areas of weakness, such as a tool for scanning developmental software to uncover design and/or implementation flaws, and leading ultimately to more reliable, robust end products.

NATIONAL CAPABILITY FOR IW INDICATIONS AND WARNING
At present, no integrated, national capability exists to detect and assess possible IW attacks in progress or preparation. Several civilian and military computer emergency response team centers have evolved, however, to provide expert diagnosis and recovery assistance for computer systems and networks that have been attacked and seriously affected by hostile actions. There is a need to detect and counter such attacks before costly information corruption and network damage occurs.
It is recommended that a National Capability Center for Indications and Warning be formed, capable of continuously gathering and analyzing monitoring data derived from government as well as commercial infrastructure systems. The center should be charged with searching for and detecting early signs and precursors of a wide scale, coordinated attack and providing warnings to U.S. government and private sector organizations. Towards that end, a phased approach is recommended, beginning with a DoD-specific organization which is scalable and extensible, and evolving towards a pan government and private sector organization. Roles of the organization should include gathering and analysis of voluntarily contributed data, dissemination of findings, and acting as a clearing house to coordinate feedback and responses from the community. The center should also act as focal point for conducting R&D on techniques and tools for attack detection and analysis. As an initial, limited scale pilot program, an interconnection of existing DoD emergency response centers should be considered.

MONITORING AND SURVEILLANCE
Current technology to detect, monitor and characterize local penetrations and wide scale attacks on the National Information Infrastructure (NII) is inadequate. A wide scale, coordinated, multifaceted IW attack on the national information-dependent infrastructure represents a major distributed measurement and analysis challenge. In order to detect attacks of such scale and likely degree of subtlety, it will be necessary to extract and correlate data across many sites, since measurements at any single site may not be sufficient to reveal the emerging overall pattern. The types of attack mounted may involve techniques and degrees of sophistication beyond simple, standard intrusion detection tactics.
It is recommended that an investment be made in developing a distributed monitoring and surveillance strategy for large scale networks, along with an associated set of supporting network architectural and instrumentation principles. Further, it is recommended that a broad based research and development effort be established to develop: 1) flexible, field modifiable, trainable tools to leverage human network and security administrators in filtering network audit data, discriminating between normal and abnormal behavior, and recognizing network attacks; 2) applied pattern recognition techniques (e.g., statistical model based, or neural net) capable of adaptation, learning and coping with temporal pattern sequences; and 3) techniques and strategies for automated, collaborative, distributed pattern recognition and problem solving, supporting the correlation and exploitation of data gathered across multiple sites in a large scale network.
There is a critical need to develop, evaluate and transition intrusion detection technology and methodology to critical infrastructure systems, in particular telecommunication systems. To meet this need it is recommended that significant R&D efforts be focused in 1.) development and investigation of techniques for cooperative intrusion detection in large scale heterogeneous networks characterized by different transmission speeds, different networking technologies and various security policies 2.) development of analysis and evaluation techniques and standard metrics for intrusion detection systems 3.) development of models to characterize IW attacks 4.) development of techniques for automatic response to incoming attacks. Such techniques should include strategies for degraded modes of operation, determining attack origin and restoral of services.
Specific emphasis should be given to demonstrating and transitioning results of the development efforts to the telecommunications and other critical infrastructure industries. This will involve adapting technologies for specific environments and evaluating and demonstrating performance in realistic scenarios and testbeds.

DAMAGE ASSESSMENT
In order to determine the appropriate response for a detected attack, it is important to correctly assess the associated damage. Failure to correctly assess damage could lead to costly over reaction (e.g., removing operational systems from service and/or unnecessarily rebuilding software and data bases), or dangerous under reaction (e.g., attempts to continue operations with corrupted data and software). Currently, there are no proven methods for reliably assessing the extent and nature of damage associated with information warfare attacks.
It is recommended that research and associated tool development be pursued with the objective of producing acceptable measures and techniques for damage assessment of both technological and business assets. These tools need to be able to assess damage at multiple levels, from application to networks, and to coalesce the results of the assessments at these levels. It is also recommended that secure logging tools and standard instrumentation packages for damage assessment be developed, which can be provided to all DoD sites where they are needed. Attention will have to be paid to adequately protecting such logs from tampering by an intruder. In addition, to coherently understand and deal with existing and potential future damage, it should be part of damage assessment to locate fault/intrusion sites for containment and purging purposes.
An important sub-problem in damage assessment is to identify information system components which remain undamaged and operational. Those components must be used to continue operations, as well as to help in the damage assessment process. Reliable damage assessment methods are needed for the information warfare communities and for other government and business interests, for a wide range of threats.
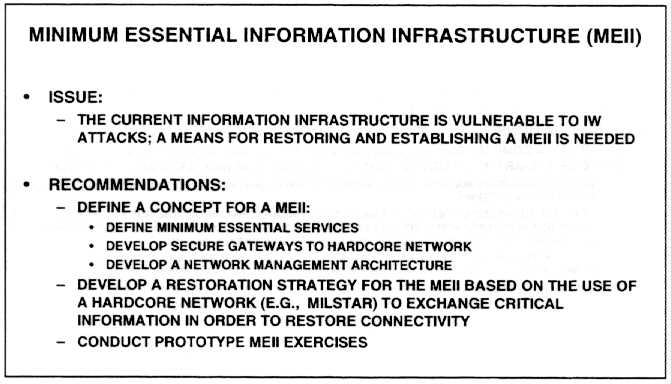
MINIMUM ESSENTIAL INFORMATION INFRASTRUCTURE
The current information infrastructure which supports telecommunications, power, transportation, etc., is susceptible to IW attacks, and in particular to wide scale coordinated attacks aimed at disabling or disrupting government as well as commercial systems. It is recommended that a strategy and overall architecture concept be developed for a minimum essential information infrastructure which can serve as a means for restoring services and adapting to wide scale outages. The technical feasibility of using Milstar assets as a means for determining available connectivity and providing modest but critical packet data service for exchange of routing, node status, and other essential network management information, should be investigated. In this role, Milstar would be supplemented with available commercial resources as possible and as needed.
The concept should consider the applications and deployment of secure gateways connected to Milstar ground station equipment and re-allocated Milstar assets as a hardcore network for use in restoring critical connectivity. The authentication of commercial wireline and wireless network access through the gateway to the hardcore network is a critical issue which must be addressed.
In addition to an overall MEII architectural concept, minimum essential services, an operational concept, and a management structure must be developed. A strategy must be developed for transitioning from peacetime or normal operational activities to the minimum essential information infrastructure. It will be important to execute the transition strategy in the context of exercises.
This activity spans government, industry, and private interests, therefore it is recommended that an organization like NSTAC be commissioned to develop and define the concept of an MEII in cooperation with the DoD.
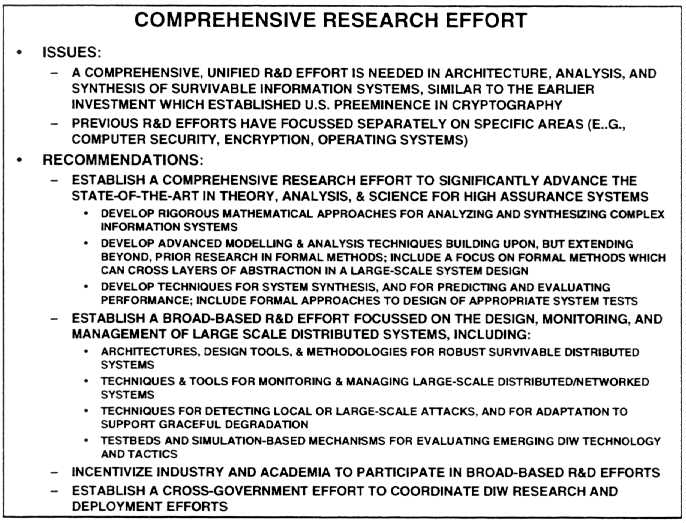
COMPREHENSIVE RESEARCH EFFORT
The development of robust survivable distributed systems resistant to information warfare attack, as well as other types of failure, requires major advances in theory, modeling and technology, and the combined efforts of a vigorous research community embracing academia, industry and government. Prior R&D efforts have focused on specific areas, such as computer and network security, encryption technology, operating system environments with multi-level security features, and coping with benign network outages caused by single node failures, etc. Little attention has been paid to the ab initio design and implementation of systems capable of surviving willful malicious attack, or detecting and tolerating corrupted software. Even less attention has been paid to the non-ab-initio case, where the system must incorporate legacy subsystems which are not under the designer's control. A comprehensive research effort is required, similar to the earlier investment in cryptographic theory, higher mathematics and associated technology, which led to U.S. preeminence in cryptography. The area of robust survivable systems offers an opportunity for a unifying theme to constitute a broad-based research effort covering the full range of 6.1, 6.2, 6.3 research, to stimulate fresh and/or revolutionary ideas and comprehensive problem solutions.
A fundamental and essential underpinning of any proposed technology base for designing and implementing large scale, robust, survivable distributed systems is a science and associated suite of design technologies for high-confidence/high assurance systems. Ideally such a set of tools would afford designers and implementers a means for describing, constructing and verifying the anticipated behavior of a complex system at all levels of abstraction. These design technologies must be capable of capturing behavioral descriptions, system properties and design descriptions in ways which enable the timely creation and performance validation of a given system implementation. Such a capability is needed because it is impossible to either anticipate or exercise all possible interactions among the large number of constituent elements and subsystems that typically comprise any system of meaningful, real world complexity. These technologies should be bound together by a unifying, fundamental mathematical logic which would allow an integrated treatment of all hierarchies of a complex system design, from logic gates to networks of computer networks.