IW-D
The key recommendations are those which can be implemented by the Secretary of Defense. Other recommendations are included which the SECDEF should make to the Director of Central Intelligence, and those which relate to the President's Commission on Critical Infrastructure Protection or the Infrastructure Protection Task Force.
This is the most important recommendation the Task Force has to offer. Multiple lead organizations with no clear principal staff assistant have led to confusion and slow progress to date. Boards and councils are important for discussing the issues, but have not and cannot provide the needed focus. Although many of the tools used to carry out information warfare have been around for a long time, the nature of information-dominated societies and activities makes it appropriate to view information warfare as a new warfare area. Information warfare is not the sole responsibility of the Chief Information Officer, the Assistant Secretary of Defense for C3I, the Director of Central Intelligence, the Chairman of the Joint Chiefs of Staff, the Secretaries of the Military Departments, or the Service Chiefs. Each of these is, however, responsible for a portion of this new warfare area. The Secretary of Defense, however, needs a single person and office to plan and coordinate this complex activity, as well as to serve as a single focal point charged to provide staff supervision of the complex activities and interrelationships involved. This includes oversight of both offensive and defensive information warfare planning, technology development, and resources. Given the interconnected nature of the information infrastructures, it is critical that the left hand knows what the right hand is doing and that these complex activities are coordinated.
This single focal point should be required to report regularly on the state of the areas shown and provide the informed interaction to other interagency and intergovernmental IW-related activities as shown in Exhibit 6-l.
Confusion and slow progress to date Boards and councils have not provided a focus Information warfare is a new warfare area -It is not Intel, C2, CIO Charge focal point to "pull it all together" -Staff supervision of both offensive and defensive IW Action: -Designate ASD(C3I) as the accountable focal point for all IW issues
-Establish a DASD(IW) and supporting staff (ASD(C3I) lead)
|
Exhibit 6-1. Designate an Accountable IW Focal Point
The Task Force recommends that the Secretary of Defense designate a focal point for the coordination of information warfare. While the focal point could be any of the existing Under Secretaries or Assistant Secretaries, the Task Force recommends that the focal point be the Assistant Secretary of Defense for C3I. The first order of business for the focal point should be to develop a plan of action to obtain the needed capabilities. The focal point should also report the Department's IW status annually to the SECDEF. The focal point should be given authority to issue instructions. The long view suggests the eventual need for an Under Secretary of Defense for Information. While the Task Force does not make such a recommendation at this time, there was strong sentiment within the Task Force in support of organizing for the long view. The Task Force also recommends that a Deputy Assistant Secretary reporting to the ASD(C3I) be named and provided an adequate supporting staff to assist in providing the necessary staff oversight and coordination of information warfare activities. The Task Force hope is that as many IW-related functions as possible would be consolidated under this individual.
Before discussing specific organizational recommendations, this section briefly discusses what the Task Force views as necessary capabilities for IW-D. Exhibit 6-2 shows the capabilities the Task Force determined are necessary for an effective information warfare (defense) and which are not adequately addressed in the Defense Department's current information warfare (defense) planning.
1. Intelligence indications and warning, current intelligence and 2. Operations (911) 3. Planning and coordination (411+) 4. System, network and infrastructure design 5. Independent assessments
|
Exhibit 6-2. Organize for IW-D
Section 3, Observations, addressed the need for intelligence indications and warnings, current intelligence, and threat assessment. A specific recommendation which addresses the needed improvements in intelligence support to information warfare (defense) follows.
"Operations" as used in Exhibit 6-2 is shorthand for those time-sensitive activities necessary for dealing with an actual intrusion or attack. While not fully analogous, the Task Force sometimes refers to these capabilities as 91l or emergency response capabilities. Remember that these operations capabilities must be distributed throughout the Department--down through the Military Departments and Services and the Defense Agencies and through the CINCs to the operating forces.
"Planning and coordination" is shorthand for preparedness activities. The Task Force has taken to referring to these capabilities as enhanced 411 or 41l + capabilities. Once again, the analogy is not completely accurate since it does not convey what will certainly be a broader interactive capability, but it does help to make quick associations with intended capabilities.
One of the more critical needs is a continued capability to obtain an independent assessment of our information warfare (defense) posture. While these assessments can be carried out at any level, it is felt that there should be a capability established which is accountable directly to the SECDEF/DEPSECDEF. In addition, the organization established to provide this capability should be staffed with people who are knowledgeable of all types of threats and of both the DoD and private sector environments.
Current intelligence resources and processes are not optimized to provide an understanding of threats and potential adversary capabilities to conduct Information Warfare; nor are they presently capable of providing either Indications and Warning or Attack Assessment of Information Warfare. An understanding of the IW process and indications of an IW attack will most probably require an unusual amalgamation of otherwise seemingly unrelated sets of data. The lack of previously identified and validated indicators for IW creates several additional difficult dimensions to the problem facing the Intelligence and Defense communities' efforts to understand all aspects of IW.
The United States has, over nearly four decades, identified many sets of data comprising indicators of activities by potential adversaries (communist-bloc). These indicators have provided the foundation of our intelligence assessment and indications and warning processes. Examples of these include known and understood development processes and cycles for military equipment's ranging from ICBMs to submarines to bomber aircraft. Thus, if we observed earth spoil on overhead imagery indicating a possible new heavy ICBM silo was under construction, we could adjust our threat understanding accordingly. Similarly, we might observe Soviet Missile Range Instrumentation Ships moving toward areas of the Pacific Ocean known (from prior observations) to be used by Russia as an impact area for ICBM tests; and we would conclude that a missile test was in the offing. Or, if a Mediterranean nation began to import chemicals which could be used either in fertilizer or in chemical agents for war; we could be on the alert for other indications of chemical gas production such as special buildings, storage facilities or personalities known to possess technical knowledge necessary to produce chemical weapons.
In a more operational vein, over time, we began to understand communist-bloc strategy, doctrine, and tactics as well. All of this knowledge was gained from a series of observations over several years. We were able to use this knowledge as we planned for combat and designed and executed wargames. Over four decades, with the expenditure of billions of dollars for collection, analysis, and reporting systems were optimized to deal with these known, discrete indications of activity. These "known indicators" permitted us to conduct intelligence assessments, Indications and Warning, and in some cases, attack assessments.
There were several factors involved in our gathering these data sets. The first is that we (and others) have made enough similar observations to establish "patterns of activity." Secondly, these observations have either caused us, or permitted us, to identify a number of discrete activities that we conclude are indicative of the "entire pattern," or significant segments of the pattern. Thirdly, having noted one or more of the discrete indicators, we know what other indicators to look for to corroborate our suspicions.
Information Warfare is a whole new game from the Intelligence dimension. We have precious few real data from which to derive "patterns of activity." This is made all the more difficult because so many of the "indicators" we have used in the past have involved some physical phenomena. In IW, at least in the computer and networked components of it, evidence of IW is fleeting at best and is usually not physically observable. The Intelligence Community is working hard to address some of these issues; but progress is hampered by organizations, processes, and systems optimized for situations found in the past, not the future. Evidence of IW preparations or attacks is most likely to come from a wide variety of sources and venues: from the more than 50 Computer Emergency Response Teams (CERT) around the world, from nodes of different segments of our National Information Infrastructure, from academia, from the Internet, from law enforcement agencies, from FEMA, and of course from traditional Intelligence Community resources such as human, signals, and open source intelligence. The Defense Science Board believes that some new approaches to collection and analysis are urgently needed.
The intelligence community understands as well as any that they face a tremendous challenge in developing information-age intelligence support activities. Some of the Task Force observations regarding these challenges were discussed earlier in the report and are shown in Exhibit 6-2-l . It is no easy matter to pinpoint the requirements, identify observables, establish patterns and indicators of the patterns, identify sources of the indicators, or determine how the sources will be exploited to collected information necessary to develop the indicators.
|
Functions - Identify requirements, observables, patterns, indicators, sources, collection Action: SECDEF formally request the DCI: - Establish an I&W/TA center at NSA with CIA and DIA support
Action: SECDEF -Direct development of IW Essential Elements of Information (EEI) |
Exhibit 6-2-1. Establish a Center for Intelligence Indications and Warning,
Current Intelligence, and Threat Assessments
The recommendation to establish the center at NSA recognizes their role in electronic intelligence and is meant to build upon recent organizational efforts at NSA. However, NSA must be augmented by DIA and CIA personnel because of the extensive social engineering component of information warfare. The Task Force believes it is essential to keep separate the intelligence and operations functions. The reason for the separation is that these functions are different. The intelligence community focuses on strategic warning and the operations community focuses on continuity of service and the warning and response to immediate danger.
The Task Force believes the recommendations in Exhibit 6-2-l are key to improving the intelligence support to defensive information warfare. While there has been some activity in these areas, the whole process needs a significant jump start. In addition, representatives from the intelligence community pointed to the lack of Essential Elements of Information (EEIs) from the operational community as a contributing factor to the intelligence challenge. This should not be an inhibitor to progress.
There may, in fact, be a need to form a National Center for Indications and Warning. This center would gather and analyze monitoring data continuously. The data would be derived from commercial infrastructure systems as well as government. The center could be charged with searching for and detecting early signs and precursors of a wide scale, coordinated attack and with providing warnings to U.S. government and private sector organizations. Toward that end, a phased approach would be appropriate, beginning with a DoD-specific organization which is scalable and extensible, and evolving towards a pan-government and private sector organization. Roles of the organization should include gathering and analyzing of voluntarily contributed data, disseminating of findings, and acting as a clearing house to coordinate feedback and responses from the community.
The basic required defensive information warfare operations functional capabilities are shown in Exhibit 6-2-2. The terms tactical warning and attack assessment are familiar to the strategic nuclear forces. They fit in the information warfare context consistent with the definitions in Joint Pub 1-02, Dictionary of Military Terms. Providing these capabilities in the information-age context, however, is very different than the nuclear era. Emergency response and infrastructure restoration are self-explanatory.
|
Functions - Tactical warning (monitor, detect, report) Support CJCS initiative to establish - Military IW operations center (J3 cell, Joint Information Warfare
- CINC IW cells
Action (ASD(C3I) lead with CJCS support): -Establish a DoD IW-D operations center (911) at DISA with NCS,
-Interface with Service and Agency capabilities and I&W/TA support |
Exhibit 6-2-2. Establish a Center for IW-D Operations
The Chairman has already undertaken an effort to establish a military operations center and has instructed the CINCs to establish IW cells within their staffs. The military operations center will consist of two elements. First, a small cell will be established in the J3 and will be staffed during normal duty hours. During crises, the J3 cell will have specific authorities over the second element, the Joint Information Warfare Center. The Joint Information Warfare Center will be staffed 7 days a week, 24 hours a day, and will serve as the interface to organizations such as the CINC IW cells, the Joint Spectrum Center, the Joint Warfare Analysis Center, the Joint Command and Control Warfare Center, and the Service IW organizations.
The distinction to be made between the military IW center and the defensive information warfare operations center is that the military center will focus on military operations of a time-sensitive nature. The defensive information warfare center will be focused on the Defense Information Infrastructure and other critical infrastructures as appropriate.
While the Task Force recommends that the center be established at DISA, current technology certainly provides for establishing a virtual center. This virtual center would draw on support from geographically dispersed elements. Initial staffing should come from existing assets. As suggested earlier, this operations capability must be distributed down and throughout the Department, linking, for the most part, existing operations centers, emergency response teams and so on. The Task Force envisions eventual links to other government centers including any that may result from the actions of the Infrastructure Protection Task Force recently created by Executive Order 13010.
Establishing the center is relatively easy. Developing and implementing the process and procedures to be used will be much more difficult; there has been almost no effort devoted to this area. One suggestion the Task Force makes is that eventual staffing and procedures take advantage of technical expertise available in the national guard, the reserves, mobilization augmentees, and contractors. Mandatory reporting sounds easy but may be difficult to implement because of a basic fear by those reporting that they will be held accountable for the intrusion or incident and that they will have to pay to fix the problem. Mandatory reporting may have to be accompanied with some form of inducements such as a "fix it free" offer. It will also be necessary to distribute these capabilities throughout the Department and establish an information channel with the indications and warning/threat assessment center for sharing of information essential to the performance of each center's mission.
If national-level centers for infrastructure protection are established as a result of the recommendations of the President's Commission on Critical Infrastructure Protection, then the Department should ensure appropriate interfaces are established between DoD functions and these centers.
The tentacles of this Operations Center should be virtually extended to every organization in DoD, ranging in scope from a single person serving as point of contact for the organization to having an emergency response cell located with the organization.
DISA should establish a threshold of information event that requires reporting to the Operations Center. Every information event reaching that threshold must be reported and penalties established to enforce that reporting. DISA should maintain a knowledge base of that reporting and ensure all response personnel are appropriately trained and informed.
The role of the planning and coordination center, shown in Exhibit 6-2-3, will be to support the ASD(C3I) in fulfilling his responsibilities as the focal point and to facilitate the sharing of sensitive information within the Department, among the Federal departments and agencies, and with the private sector.
Functions - Develop IW planning framework
- Develop procedures and metrics for assessing infrastructure and Action (ASD(C3I) lead): -Establish an IW-D planning and coordination center (411+) reporting to
|
Exhibit 6-2-3. Establish a Center for IW-D Planning and Coordination
One of the first activities of the planning and coordination center should be to establish a planning framework which can provide for meaningful assessments of progress in information warfare preparedness. This center will not write plans for the CINCs, Services, and Defense Agencies, but will identify the need and means for integrating information warfare considerations into traditional planning activities.
The center will aid the focal point in assessing the treatment and implications of information warfare in policy and plans, operations, and the allocation of resources to information warfare. The center will also analyze and assess IW-related incident reports generated by the Services and Agencies and forwarded to the 91l operations center. The assessment will determine patterns of activity that might indicate the need to revise plans or resource allocations.
Since there is no established method for assessing the dependency of operations plans and DoD support activities on information and infrastructures, the center will need to develop the procedures and metrics for such assessments. The military operations community and the functional support community will perform the assessments. These infrastructure dependency assessments will be discussed in more detail later in this report.
Sharing of sensitive information is probably one of the most important first steps in building a defensive information warfare capability. There are significant legal, regulatory, competitive and emotional hurdles to overcome; these must be addressed as soon as possible.
It is not necessary to break the cryptographic protection to attack our classified computing environments. The protection paradigm used by DoD is based upon the classification of information. However, most classified computer systems contain, and often rely on, unclassified information. This unclassified information often has little or no protection of the data integrity prior to entry into classified systems. The expected interaction between GCCS and GTN are examples of this. An increasing number of DoD systems contain decision aids and other event-driven modules. These should be buffered from unclassified data whose integrity cannot be verified.
Second-, third-, and "n" -order effects from an information warfare attack
have not been observed and are not well understood. Further, good data are
not available with which to conduct modeling and simulation of such effects.
Data must be collected to support the modeling and simulation of the effects
of specific information warfare attacks and defenses. Detailed data should
be gathered through several means:
To achieve the goal of protecting information systems from future IW attacks, a comprehensive, principled approach for architecture, design, and analysis of secure, survivable distributed information systems must be developed. These new principles and approaches should build upon, and be synthesized from, existing and emerging information system engineering principles based on work in fault-tolerant systems, trusted systems, and secure distributed systems. The principles must be promulgated as guidelines so that they will be widely applied.
There is a need to create a broader theoretical underpinning for understanding, design, and analysis of the security and survivability of information systems. Theoretical tools available today usually treat specialized aspects of information security. Early information-theoretic work in the 1950s and 1960, work in the 1980s on trapdoor functions, and recent work on Byzantine robust networks may form some basis for development of a broader theory. New theories should be developed for robust systems. These theories need to include models both for attacks on systems and for survivability defense strategies. Robust system theory should include formal methods that apply to large-scale, distributed, heterogeneous systems. Analysis techniques should include methods for predicting and analyzing Red/Blue conflicts by, for example, extension/application of game theory and other relevant approaches.
Since the cost of highly secure network subsystems will be very high, the architect should assume that the defense network will traverse commercial infrastructures, and that the underlying substrate will be inherently insecure. The network architecture thus must ensure successful transmissions in the presence of failed, faulty, and spoofed network components. For example, spatial transmission diversity is an existing proof that reliability can improve with intelligent use of the network. Since the future global network will include subnets of varying robustness, it is suggested that a separable entity be established as an overall net security management system. The overall network security manager would be responsible for architectural add-ons (such as wrappers) for each subnet, to provide survivable, secure service over the entire net of nets.
For survivable systems, security is required at multiple levels, including applications, middleware, operating systems, and networks. New architectural approaches must enable the accommodation of legacy and COTS subsystems, perhaps via wrappers, into an overall adaptive system-of-systems architecture. This architecture must be designed to reallocate critical tasks dynamically to subsystems which have survived the attack. The security/survivability management of the system should be integrated into the overall system management framework, in terms of both the automated and the human components of the system management structure.
In order to test the effectiveness of the survivable system architecture, principles, and theory, it is essential to conduct experiments and demonstrations. It is recommended that such experiments and system demonstrations be conducted in existing and emerging system testbeds and networks, building on both experimental nets and the emerging DII and NII.
There are substantial differences between designing a typical information system and designing a resilient information infrastructure capable of enduring in the face of intentional disruptions. Information system design is typically based on efficiency; a resilient information infrastructure design must be based, instead, on effectiveness. Control must be decentralized and portions must operate independently of the infrastructure. For example, fault-tolerant computing introduces redundancy into otherwise efficient systems in order to make them more effective, particularly against random disruptions. Similarly, the design of a resilient infrastructure will ensure diversity of hardware and software so that a common failure mode will not result in an infrastructure failure. Investing in a proper design up front saves money in the long run and negates the very real possibility of introducing vulnerabilities by attempting to retro-fit security.
The goal is to design for utility, resiliency, repairability, and security, as shown in Exhibit 6-2-4. Presently, there is no significant body of knowledge on infrastructure design. It will have to be developed based on the existing design skills for fault-tolerant computing, resiliency, reliability, and so on. This body of knowledge will expand through on the results of the research currently under way and planned for large distributed networks and survivable systems. This growing body of knowledge will be used to develop and promulgate policies, architectures, and standards which enhance the utility, resiliency, repairability and security of the infrastructure. The collection of these policies, architectures, and standards will constitute the infrastructure design.
Functions - Develop and promulgate policies, architectures, standards
- Develop and implement configuration management process Action (ASD(C3I) lead): -Establish a joint security architecture/design office within DISA to
|
Exhibit 6-2-4. Establish a Joint Office for System, Network and Infrastructure Design
The infrastructure design should be verified independently periodically to ensure that the design meets the goals of utility, resiliency, repairability, and security. The Task Force suggests using NSTAC, NCS, and similar resources to aid in this activity.
The infrastructure design should also be used to verify that goals of utility, resiliency, repairability, and security are reflected in the specifications for development of new systems and for purchase of services from the other government agencies and the private sector.
The Task Force recommends the establishment of a joint architecture/design office in DISA to develop and promulgate throughout the Department the needed design policies, architectures, standards, and configuration management process. This office should include the current architecture and design activities of DISA, but should also be focused on infrastructure design and the incorporation of security up front in the architecture and engineering process. The Task Force also recommends that a process be developed to verify compliance with the design independently.
Red Teaming is an essential component of the IW-D strategy and technology development process. We recommend that the concept be extended to include vulnerability analyses as well as carefully planned attacks during experimental activities in controlled testbeds and during training/planning exercises. The Red Team exercises should be conducted under proper rules of engagement to avoid unnecessary damage or disruption to information systems.
Emphasis should be given to developing new attack methodologies in addition to reusing and applying of current attacker techniques. For example, attacks should be designed which exploit the system's survivability features. A sophisticated attacker would probably know about these features. In formulating these attack strategies, models should first be developed for system vulnerability and its likely defenses, and these models should be exploited in the attack strategies. Vulnerability analyses and Red Team attacks should be conducted at the application and system level, as well as at the subsystem level, with the goal of uncovering how operations can be perturbed (e.g., the planning and execution of an air tasking order or the deployment of sensors and communication assets), and how supporting communication links, or specific computers and network nodes, can be compromised.
The need for independent assessments is suggested in the notion that "you can only expect what you inspect." Many activities throughout the Department are in the process of forming Red Teams for the purpose of conducting vulnerability analyses, training, readiness assessments, and so on. The Task Force endorses these efforts, particularly in light of previous DSB Task Force recommendations. However, what the current Task Force is recommending is the "SECDEF/DEPSECDEF's Own" -- a team whose central role is providing the SECDEF/DEPSECDEF with unbiased assessments on the Department's IW "state of health."
As shown at the bottom of Exhibit 6-2-5, the Task Force recommends that a Red Team be established to perform these independent assessments. Two previous Defense Science Board Studies have made a similar recommendation to establish such a Red Team. While the Task Force was unable to agree on whether the new organization should be a standalone organization or housed in an existing organization, there was unanimity on the fact that the Team will require significant management attention and, although reporting through the ASD(C3I), be accountable to the DEPSECDEF for its activities.
Functions - Acquisition - assess vulnerabilities
- Operations - conduct "IW-like" attacks
-Spectrum of attacks
Action (ASD(C3I) lead): - Establish a Red Team
- Tight leash and significant management attention -Develop procedures for employment of the Red Team
|
Exhibit 6-2-5. Establish a Red Team for Independent Assessments
Developing and maintaining an independent assessment capability is very important because of the traditional resistance to self-assessment and potential embarrassment. However, it is essential that the Department evaluate its IW preparedness and not wait to learn of any major shortfalls because of the actions of an adversary. This Red Team should have a small permanent cadre for management and technical continuity and should be staffed by civilian personnel and military personnel on a rotating joint duty basis.
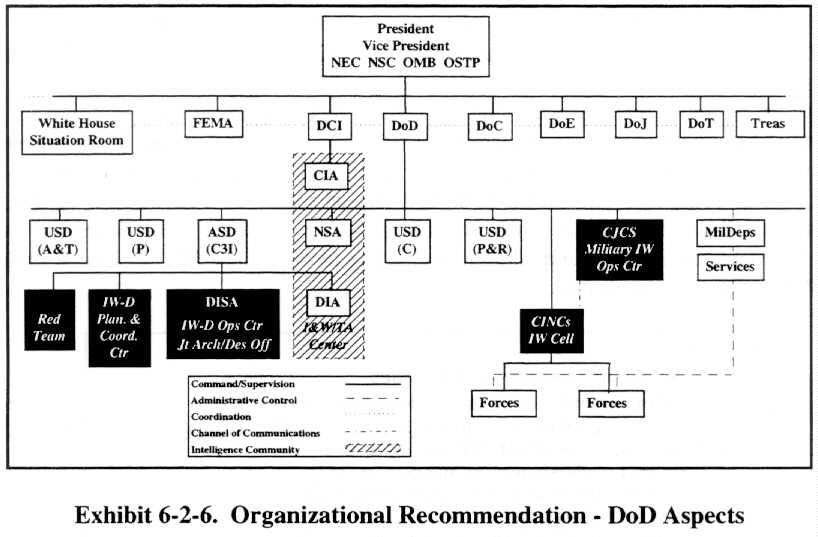
The organizational recommendations made by the Task Force are shown graphically in Exhibit 6-2-6. While it was obvious to the Task Force that similar information warfare (defense) capabilities and organizations must be established at the national level, the Task Force decided not to make specific recommendations about where these organizations should be established or to whom they should report. Instead, the Task Force recommends this be left to the President's Commission. However, it should be pointed out that there is a real need for extensive coordination and information sharing between government (Federal, state, and local) and the private sector.

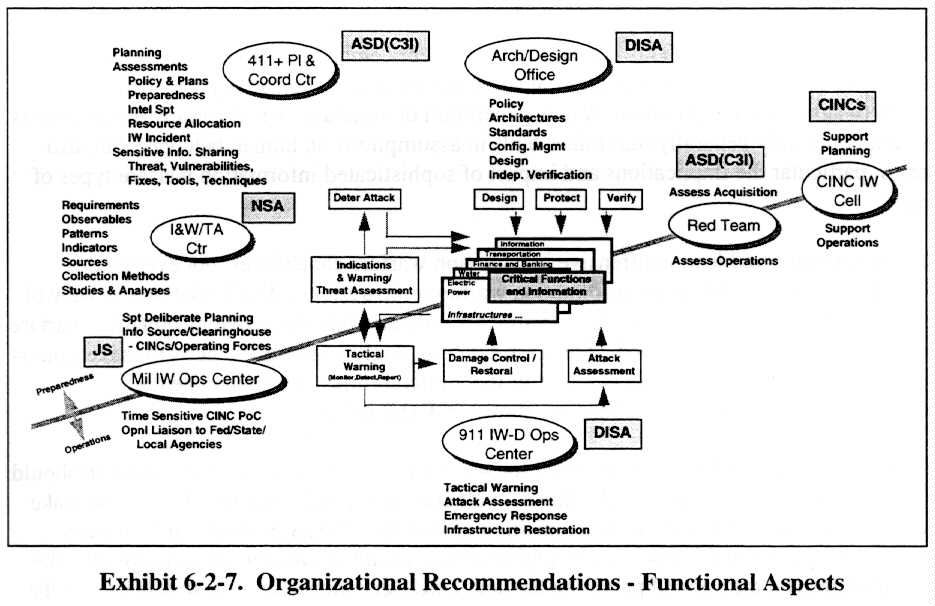
Exhibit 6-2-7 also shows the organizational recommendations made by the Task Force but emphasizes the functional aspects. The defensive information warfare process, procedures and mechanisms diagram discussed earlier in the report is shown in the middle of the Exhibit and the process has been divided by the gray line into preparedness functions and operations functions. The recommended organizations are arrayed in the Exhibit so as to relate their functions (shown near the ovals) to the entire defensive information warfare process.
An important and cost effective first line of information warfare defense is a user and operations community that is aware of potential threats and is well trained in protection, detection, and reaction tactics, techniques and procedures. A well-trained and educated cadre of security and automated information system professionals can provide an effective second line of defense. The Services and Agencies (NSA in particular) have long provided INFOSEC training. Traditional DoD security awareness and training, however, has emphasized the security of classified national security information and information systems processing classified national security information. DoD components are currently implementing awareness, training, and education (ATE) programs to focus on new threats to both unclassified and classified networks. Working groups have been established to help coordinate efforts between components. There is a need, however, for a DoD-level forum with the authority to reduce duplication and implement consolidated training responsibilities. This forum must take advantage of core competencies to ensure a comprehensive, cost-effective program.
Current modeling and simulation efforts do not adequately address issues that can be expected to arise in an information warfare attack environment. For example, little or no consideration is given to the tactical impact of compromised or exploited computing and networking resources, beyond perhaps the classical effects of jamming or ESM techniques as applied to the battlefield communications infrastructure.
A fundamental shortcoming of traditional wargame-oriented simulations is the failure to predict changes in battlefield behavior resulting from the dynamic interplay of people with new weapons, sensors, tactics, etc. This is mainly due to deeply embedded, built-in assumptions of human tactical behavior. The introduction of a new dimension to the battle-space, namely that of IW, serves to aggravate the problem. A new generation of simulations and gaming environments is needed that not only generally minimizes built-in assumptions on human behavior, but also captures in particular the implications and impact of sophisticated information warfare types of attacks.
Because of our perceived lead in offensive information warfare capabilities, not everyone understands the need for defensive information warfare preparations. The Task Force review of several current Service and joint doctrine documents indicates that defensive information warfare matters are not adequately addressed. The Task Force strongly suggests the need to make senior-level government and industry leaders aware of the vulnerabilities and appreciate the implications. The recommended actions are shown in Exhibit 6-3.
The awareness campaign should be designed for several purposes. The internal campaign should make DoD personnel more aware of the threats, vulnerabilities, and fixes and should also make DoD a better informed customer in the acquisition of systems, COTS products, and services. The external program should make DoD suppliers better aware of DoD needs and should make the civil agencies and the general public understand DoD dependence on infrastructures and the role of DoD in the information-age "common defense."
IC/IW (Offense) capability breeds complacency Military doctrine does not adequately address IW vulnerabilities Need senior-level government and industry appreciation of what's at stake -Pursue all avenues (briefings, conferences, articles, etc.) Action: - Establish an internal and external IW-D awareness campaign for the public, industry, CINCs, Services and Agencies (ASD(C3I) and Public Affairs)
|
Exhibit 6-3. Increase Awareness
The Task Force recommends that the ongoing IW net assessment recommended by the 1994 Summer Study be expanded to include an assessment of the vulnerabilities of the DII and the NII with particular emphasis on those portions of the NII upon which the Department is especially dependent. A brief review by the Task Force of selected joint doctrine revealed a heavy dependence on information and information technology without corresponding attention to defensive information warfare. Existing doctrine should be reviewed for needed emphasis. The Department should also explore the possibility of large-scale demonstrations for the purpose of exploring cascading effects and for collecting data necessary for simulation of information warfare activities.
In addition and to the extent possible, information warfare (defense) must be realistically played in exercises. This will require some concerted management attention. The Task Force notes that since 1992, DoD policy has called for military exercises to include realistic information warfare play. To date, there has been very limited execution of this policy. In those cases where a realistic IW environment cannot be created, specific experiments should be developed to assess the effects of information warfare attacks. For example, policy directing the CINCs to conduct exercises with information warfare realism has been effect since 1992 and there has been no noticeable efforts to date to implement the policy. In those cases where such realism is not possible, specific experiments must be developed to assess the effects of information warfare attacks.
Traditional thinking is that infrastructures, with few exceptions, are stable, reliable, and always available. The nation's interstate highway system is a prime example. Consequently, the Departments' operational and functional planners have not adequately addressed the possibility that key infrastructures such as telecommunications, electric power, and transportation might not be available in part to support military operations. The purpose of this recommendation, as shown in Exhibit 6-4, is to get the operational and functional planners to begin documenting the extent to which their plans are dependent on critical infrastructures and what effect infrastructure disruptions might have on execution of the plans.
Dependencies and vulnerabilities not well understood - Affects efforts to mobilize, deploy, employ, control and sustain forces
The Mission Needs Statement for Infrastructure Assurance Modeling Action: - Develop a process and metrics for assessing infrastructure dependency
|
Exhibit 6-4. Assess Infrastructure Dependencies and Vulnerabilities
The Joint Staff has begun to address the issue by developing a draft Mission Needs Statement for Infrastructure Assurance Modeling. The MNS approach is to use modeling and simulation. This is probably the best long-term approach to understanding infrastructure inter-dependencies, potential cascading effects, etc.
The Task Force recommends that a separate effort be initiated by the ASD(C3I) to develop an alternative approach using other analytical techniques that could be employed in the near term by the operational and functional planners to assess all critical infrastructure dependencies. Based on these assessments by the Chairman and the Principal Staff Assistants, the Chairman should develop the essential infrastructure protection needs and the ASD(C3I) should develop the resource estimates for the needed protection.
The Task Force recognizes that this will be an enormous task. However, the complexity and difficulty of the task should not be an impediment to starting the effort; "the journey of a thousand miles begins with a single step."
Exhibit 6-5-1 shows that, as in the traditional operations community, the IW-D operations community requires an alerting mechanism to heighten awareness and preparedness as the threat increases. In addition, there should be some prescribed response by the IW-D operations community to increasing threat conditions such as minimizing the traffic on the networks, restricting personnel access to operational facilities, disconnecting certain systems from networks which are likely targets, and possibly implementing wartime modes of operation. While the effort is urgently needed, it will be complicated by the extensive interconnectivity of systems and networks and because some actions will be required by the private sector, in part, since much of the Defense Information Infrastructure is embedded in the public switched and data networks.
Conditions and responses required for risk management - Conditions analogous to DEFCON
Defense of the information infrastructure complicated by -Interconnectivity - heightened state of alert must extend to all connected Action: - Define and promulgate a useful set of IW-D threat conditions which is
|
Exhibit 6-5-1. Define Threat Conditions and Responses
Exhibit 6-5-2 is an illustrative cut at what a structured threat condition and response table might look like. This is not a definitive threat chart. For example, "normal" is yet to be defined and very damaging attacks can be postulated that would not cause a noticeable increase in the number of incidents. Also, it should not be inferred that the Task Force believes an information warfare attack will necessarily escalate in a linear manner from level II to level V. An attack could be oriented on a specific critical target or could immediately threaten multiple centers of gravity within the United States. The term "special contexts" is an attempt to highlight the potential linkages between an information warfare attack and other circumstances that may be present. For example, disruption of the infrastructures supporting Fort Bragg, North Carolina, would have much greater impact during a deployment of U.S. forces to a crisis location than it would during normal peace-time training operations.
| CONDITION | SITUATION | REQUIRED RESPONSE |
| I - Normal | Normal threat-crime/incompetents
Normal activities in all sectors |
Normal actions and requirements |
| II - Pertubation | 10% increase in incident reports, regional or functionally base 15% increase in all incidents |
Increase in incident monitoring
Look for patterns across a wide range
Alert all agencies to increase awareness
Begin selective monitoring of critical |
| III - Heightened Defense Posture |
20% increase in all incident reports
Condition II with special contexts |
Disconnect all unnecessary connections
Turn on real-time audit for critical systems Begin mandatory reporting to central control |
| IV - Serious | Major regional of functional events that seriously undermine U.S. interests Condition II/III with special contexts |
Implement alternate routing
Limit connectivity to minimal states Begin "aggressive" forensic investigations |
| V - Brink of War | Widespread incidents that undermine U. S. ability to function Condition III/IV with special contexts |
Disconnect critical elements from public infrastructure Implement WARM protocols Declare state of emergency |
Exhibit 6-5-2. Sample Threat Condition and Response
Deriving a solid set of threat conditions and appropriate responses will require some serious research. The various levels reflect combinatorial effects as well. For example, it is possible to move from Condition I to Condition V without passing through the intervening conditions. Condition II reflects the notion that an attack may be surgical rather than broad-based.
Information warfare defense should be viewed from a warfighting perspective. Operational forces should be able to detect, differentiate among, warn of, respond to, and recover from disruptions of supporting information services. Recovery from disruptions resulting from failures or attacks might involve repair, reconstitution, or the employment of reserve assets. In some cases, network managers may have to isolate portions of the network, including users of the network, to preclude the spread of disruption. Given the speed with which disruptions can propagate through networks, these capabilities may need to be available in automated form within the network itself. Finally, there must be some means to manage and control these capabilities. At its heart, this is an operational readiness matter.
A standardized process to enable commanders to assess and report their operational readiness status as it relates to their specific dependency on information and information services is an essential element of operational readiness. A standard vocabulary will enable common description of risk scenarios and assessment methodologies. (A more complete explanation of the proposed process is at Appendix C.) The use of a structured assessment and reporting process will help move information assurance from a global and unsolvable problem to the identification of discrete information and information service dependencies that illuminate quantifiable risk to specific information dependent activities within a commander's sphere of responsibility. A similar assessment and reporting process can be applied by supporting elements and in the commercial sector.
Exhibit 6-6 shows that information warfare (defense) must be mainstreamed as a readiness issue. A means must be developed for including information warfare (defense) issues in readiness reporting and a process must be developed to assess the information warfare (defense) readiness posture independently. The assessment scenarios differ from the threat conditions discussed earlier in that the assessment scenarios are used to assess readiness against a wide range of possible threats to specific units, missions, and functions, while the threat conditions are used to describe the existing threat condition to the broad interconnected population. The assessment scenarios are applied locally, while the threat conditions are applied globally. Standardized assessment scenarios could be used for planning considerations, in warning orders, and so on. The assessment regime provides a means for addressing variability and should be used in concept and operations planning.
Readiness assessment system - Need explicit process to tie IW-D readiness assessments to the ability
-Propose standardized, graduated assessment regime
Action: - Establish a standardized IW-D assessment system for use by CINCs,
|
Exhibit 6-6. Assess IW-D Readiness
Readiness reporting system - Need a standard IW-D preparedness reporting system using assessment Action: - Incorporate IW preparedness assessments in Joint Reporting System and
- Add IW preparedness to overall unit readiness rating (C-Level)
- Add explicit review of IW to review of Ops/Con Plans
- Address IW preparedness in new annual CSAAS cycle
- Include IW, apply to CONUS and OCONUS bases
- Add IW posture to assessment factors
- Modify to include status reporting on major computing resources
|
Exhibit 6-6. Assess IW-D Readiness (Continued)
The Task Force recommends that the Chairman of the Joint Chiefs of Staff incorporate information warfare preparedness assessments in the Joint Reporting System and into Joint Doctrine. The systems, reports and publications cited are only examples that the Task Force reviewed to illustrate how these assessments might be incorporated. Additional details will be provided in the written report.
There are a number of things the Department can undertake, as shown in Exhibit 6-7, that are relatively low cost, but that will raise the bar significantly for potential system and network intruders. Training and awareness have already been emphasized. The two specific examples are cited to illustrate the fact that there is existing Executive Branch policy regarding this matter and that the use of banners to alert users is a good way to increase awareness. Certification by users of banner understanding is another technique to emphasize the importance. One of the Task Force members cited as an example the procedure used in his company. On a periodic basis, users of the network are presented with a security awareness quiz. If the questions are not answered correctly after three tries, the user must have the systems administrator provide access to the system or network.
Training and awareness - Enforce provisions of Appendix 3, OMB Policy A-130 Improve security of DoD's unclassified computers - Access control (get rid of fixed passwords!) Promote use of government approved commercial security technologies - Support JWCA Phase 5 plan of action Action (ASD(C3I) lead: - Direct the immediate use of approved products for access control
- Examine feasibility of using approved products for identification and authentication
|
Exhibit 6-7. "Raise the Bar" With High-Payoff, Low-Cost Items
One of the most important acts is to improve the security of DoD's unclassified computers by instituting dynamic access control and authentication of users. Until this is done, the Department has little assurance that it has any control over these systems. many of which are essential to critical support functions. The Department should also promote the use of existing commercial and government security technologies.
The Task Force recommends the immediate use of commercial access control technologies for this purpose. These technologies can be used as an interim solution for MISSI and as a solution for those users not programmed to receive MISSI. The Department should also explore the feasibility of using approved commercial products for identification and authentication and continue its plans for the use of escrowed encryption, particularly for the protection of critical assets.
The current information infrastructure which supports telecommunications, power, transportation, etc., is susceptible to IW attacks, and in particular to wide-scale coordinated attacks aimed at disabling or disrupting government as well as commercial systems. A strategy and overall architecture concept must be developed for a minimum essential information infrastructure (MEII). This minimum infrastructure can serve as a means for restoring services and adapting to wide-scale outages. Milstar should be investigated as a means for determining available connectivity and providing modest but critical packet data service for exchange of routing, node status, and other essential network management information. In this role, Milstar would be supplemented with available commercial resources as possible and as needed.
The concept should consider the applications and deployment of secure gateways connected to Milstar ground station equipment and reallocated Milstar assets as a hardcore network for use in restoring critical connectivity. The authentication of commercial wireline and wireless network access through the gateway to the hardcore network is a critical issue, and must be addressed.
In addition to an overall MEII architectural concept, minimum essential services, an operational concept, and a management structure must be developed. A strategy must be developed for transitioning from peacetime or normal operational activities to the minimum essential information infrastructure. It will be important to execute the transition strategy in the context of exercises.
The minimum essential information infrastructure capability shown in Exhibit 6-8 could serve the Department for critical missions and functions and could serve the nation for other national security-related functions. The 1995 DSB Summer Study titled Investments for Century Military Superiority recommended a minimum essential C3 capability. Included are the specific recommendations leading to that capability.
Current NII/DII is vulnerable - Not designed for resiliency or repair Need -Failsoft infrastructure to support critical functions while under attack Core capabilities exist - Milstar Critical interaction of fuel, power, and telecommunications Base on infrastructure dependency assessments Build on 1995 DSB Summer Study recommendation Action: - Define options with associated costs and schedules (ASD(C3I) lead)
|
Exhibit 6-8. Establish and Maintain a Minimum Essential Information
Infrastructure
New information security products from biometric personnel identification devices to advanced firewalls are being introduced every day into the commercial marketplace. Many of the products are either focused on protecting against network-based intrusions or are attempting to enable some form of electronic commerce. However, these products often do not scale well in large distributed environments, are too expensive, and are too difficult to configure.
The Department of Defense should monitor the progress in commercial information technology and take care not to duplicate or reinvent the progress being driven by market forces. However, the commercial market will not provide the Department the necessary tools and techniques to rapidly and securely assemble and protect a robust, resilient, deployable information system to support a Joint Task Force or coalition operations. The Bosnia C2 Augmentation initiative is an example of the challenge.
As cost-affordable technologies are developed, they should be given early tests in the Joint C4ISR Battle Center Environment.
The Task Force is aware of several of the ongoing information system security initiatives under way in DARPA and has read the descriptions of other IW-D R&D efforts in the Joint Warfighting Science and Technology Plan and in the Defense Technology Objectives of the Joint Warfighting Science and Technology and Defense Technology Area Plan (both of May 1996). However, the Task Force suggests a tighter, more integrated focus on support to U.S. defense activities in the areas outlined in Exhibit 6-9. In addition, Task Force did initially consider a much broader and more comprehensive list of R&D initiatives required for information warfare defense. Because of the potential contribution of commercial activities to some of the Department's requirements, the Task Force recommends the Department should focus its R&D on those aspects of information protection and assurance not likely to be addressed by the private sector. Several Task Force members stressed that the R&D program must emphasize cost and operational realism. For example, it would be helpful if the primary design criteria included per-seat costs for installation, training, and support.
Current security products are not designed to protect large distributed
Must devote attention to verifying security configuration of a rapidly
DoD must carefully evaluate emerging commercial technologies and - To include testing in Joint C41SR environments
Focused research effort required which involves academia, industry and
-Few universities currently have related courses or research programs Action (USD(A&T) lead): - Focus the DoD R&D program on the following areas
- No one event/attack should lead to failure of a critical function
-Work with the National Science Foundation to develop
|
Exhibit 6-9. Focus the R&D
The development of robust survivable systems resistant to information warfare attack, as well as other types of failure, must involve major advances in technology and will require the efforts of a vigorous research community embracing academia, industry, and government. Prior R&D efforts have focused on areas such as computer and network security, encryption technology, and single node failures. Little attention has been paid to surviving willful malicious attack, or detecting and eliminating corrupt software.
The area of robust survivable systems offers an opportunity for a unifying
theme to develop a broad-based research effort covering the full range of
6.1, 6.2, and 6.3 research to overcome the current lack of significant new
ideas and problem solutions. Particular emphasis should be given to the following
areas:
As indicated in the previous exhibit, specific attention should be paid to verifying the configuration of a rapidly assembled system for use in Joint Task Force or coalition environments. This should include positive identification of system components with passive identification of users, in both the static and mobile environments.
Regarding test beds and simulation-based mechanisms, it will be important
to:
In addition to the above, the R&D community should also consider establishing
a focused effort on the theory, science and analysis of high assurance, massively
distributed systems to include:
Finally, the Department should work with (and even possibly provide seed money to) the National Science Foundation to establish research and education programs for resilient system design in the universities and colleges.
IW vulnerability is often due to human error, insufficient training, or lack of knowledge of or failure to follow procedures or adhere to policy. This vulnerability represents a gap which cannot be closed with technology alone. Currently, capabilities of system and network administrators and system managers vary widely. This is partially due to a lack of appropriate training, and partially due to the difficulty in use of existing security products and in obtaining information on how to configure a system securely.
A cadre of high-quality, trained professionals with recognized career paths is an essential ingredient for defending present and future information systems. It is recommended that research be conducted towards the development of techniques, curricula, tools, and technology specifically for security-focused training for system and network administrators. Developing partnerships with universities, colleges, existing DoD professional development programs, and vocational schools for the purpose of curriculum development will be an essential ingredient of this process. It will also be important to capitalize on emerging distributed interactive simulation technology to provide a realistic, dynamic, operations center-like training environment indicative of a real-world IW combat setting.
The Task Force acknowledges that there are a number of studies and initiatives under way in the area of information warfare (defense) training. Included in these is a recent NSTISSC review of training which recommended the development of a database of all available INFOSEC training courses. NSTISSC has also developed training standards for Systems Administrators, Information System Security officers, and Designated Accreditation Authorities. However, efforts throughout the Department do not appear to be well coordinated and there does not appear to be a concerted effort to train systems and network coordinators properly.
As shown in Exhibit 6-10, the Task Force recommends establishment of a skill specialty for military personnel to enable the formation of a cadre of knowledgeable and experienced defensive information warfare specialists. The skill specialty is recommended instead of a career path to ensure that operational experience is reflected in the performance of the information warfare (defense) duties and to preclude the possible formation of a closed community of experts.
Systems/network administrators are the first line of defense - Need a professional cadre - not "other duties as assigned" Need IW-D skills and awareness in all functional areas Action: -Establish a career path and mandate training and certification of systems
|
Exhibit 6-10. Staff for Success
Legal issues can be a distraction from moving on with what can be done. As shown in Exhibit 6-11, the Task Force found some confusion among the Department's representatives regarding the scope of their authority to monitor systems and networks for the purpose of assessing the security of the systems and networks. As discussed earlier, the advent of distributed computing has and will continue to blur the boundaries of the systems and networks that DoD uses. Confusion also stems from uncertainty over when or whether a wiretap approval is needed. All DoD system and network administrators should assume that any intrusion is a hostile intrusion and take action to minimize the effects of the intrusion and report the intrusion for purposes of tactical warning and to obtain necessary protective support, including law enforcement.
Issues: -Defending DoD systems
-Defending other government and civil systems
- DoD assistance to the private sector (e.g. Computer Security Act) Action (General Counsel lead): -For DoD systems, promulgate:
- Provide to the Presidential Commission on Critical Infrastructure
|
Exhibit 6-11. Resolve the Legal Issues
To lessen the confusion, the SECDEF/DEPSECDEF should direct the General Counsel to explore this matter and issue rules of engagement regarding appropriate defensive actions that may be taken upon detection of intrusions into and attacks against DoD systems and networks. This should include promulgating clear guidance regarding monitoring of systems under DoD control and the use of warning banners on these systems.
The SECDEF/DEPSECDEF should also task the General Counsel to propose legislation. regulation, or executive orders as may be needed to make clear the DoD role in defending non-DoD systems. This should specifically address the need for changes to the Computer Security Act, the capture of information on unidentified intruders (issue of intelligence collection on U.S. persons), the authority to conduct "hot pursuit" of intruders, and the ability to obtain reports from the operators of critical elements of the civil infrastructure.
The findings and recommendations developed by the General Counsel should be provided to the President's Commission to aid in their deliberation of the legislative and policy initiatives required for the protection of the critical infrastructures.
Exhibits 6-12-l through 6-12-4 indicate the Task Force recommendations regarding what DoD should offer to, advocate to, request from, and suggest to the President's Commission. Exhibit 6-12-1 suggests what capabilities DoD might offer to the Commission and the nation in support of critical infrastructure protection. The Department should think through and propose to the Commission appropriate national defense response and retaliation capabilities in the event of an information warfare attack on the critical civil infrastructures, understanding that Defense is not the sole element in responding to threats to the national security.
Action: Offer DoD capabilities to the President's Commission (USD(P)and ASD(C3I)): - Improve private sector defenses
-Provide IW&TA to private sector
- Restore service to critical infrastructures
-Response/Retaliation/Deterrence
|
Exhibit 6-12-1. Participate Fully in Critical Infrastructure Protection
Exhibit 6-12-2 suggests what DoD interests should be advocated before the Commission. The information-age war powers for the President are suggested in light of the outdated nature of Section 706 of the Communications Act of 1934. This Act is the basis for Federal intervention in assuring the operation of the telecommunications infrastructure. Critical infrastructure assurance goals can be articulated in a general fashion, but should be eventually based on the infrastructure dependency assessments discussed earlier in the report.
Action: Advocate DoD interests to the President's Commission (USD(P) and ASD(C3I)): - Continued clarity of responsibilities of the Commander-in-Chief and SECDEF in any policy proposed by the President's Commission
|
Exhibit 6-12-2. Participate Fully in Critical Infrastructure Protection (Continued)
In addition, there are many international aspects of information warfare
that must be addressed as the U.S. formulates a defensive information warfare
strategy that will guide DoD operations. For example:
Exhibit 6-12-3 shows what DoD needs from the President's Commission.
Action: Request the President's Commission provide DoD (USD(P) and ASD(C3I)): - Essential critical infrastructure protection
- Coordinated infrastructure design theory, research, principles, and guidelines
|
Exhibit 6-12-3. Participate Fully in Critical Infrastructure Protection (Continued)
Recognizing the difficulty of defining an appropriate role for the government and the private sector in critical infrastructure protection, the Task Force offers these suggested roles which DoD could provide to the Commission. These suggestions are based on input to and deliberations by the Task Force and individual panels of the Task Force. Exhibit 6-12-4 suggests such roles.
Action: Suggest IW-D roles for government and the private sector to the President's Commission (USD(P) and ASD(C3I)):
- Government
- Establishing infrastructure assurance goals
- Regulatory relief
- Government (Continued)
- Awareness (Informed self-protection, not government sponsored solutions) Threats, vulnerabilities, fixes, tools, techniques, intrusions - The "common defense" Research, advice, training, back-up support, registry of knowledgeable personnel - Disaster assistance
- DoD and other government emergency response teams
- Private Sector
|
Exhibit 6-12-4. Participate Fully in Critical Infrastructure Protection (Continued)
The NSTAC Model for Government-Industry Cooperation Establish necessary programs (e.g., GETS, NTMS, TSPS, CPAS) Share sensitive information (e.g., NSIEs) Exchange general information (e.g., R&D exchange) Review/generate requirements for security stds (e.g., NSSOG, SLG) Conduct risk assessments (e.g., PSN, Electric Power, Finance, Transportation)
Participate in games and exercises ("The day after..., natural disaster
exercises, Enhance awareness of vulnerabilities/threats (Outreach activities) Develop principles/standards for products~services (NIITF ISSB) Coordinate crises operations (NCC)
|
Exhibit 6-12-5. Participate Fully in Critical Infrastructure Protection (Continued)
The NSTAC model shown in Exhibit 6-12-6 could serve as a model for refining the roles of government and industry as suggested here. Sensitive information includes threats, vulnerabilities. intrusions and other incidents. fixes to vulnerabilities. etc.
Exhibit 6-12-6 suggests a model as a starting point for refining the government and private sector roles.
Personal |
Business |
Public |
Government |
National |
|
| Incompetent | O |
O |
O |
G |
G |
| Hacker | O |
O |
O |
G |
G |
| Disgruntled Employee | O |
O |
O |
G |
G |
| Crook | O |
O |
O |
G |
G |
| Organized Crime | O/G |
O/G |
O/G |
G |
G |
| Political Dissident | O |
O |
O |
G |
G |
| Terrorist Group | O/G |
O/G |
O/G |
G |
G |
| Foreign Espionage | O/G |
O/G |
O/G |
G |
G |
| Tactical Countermeasures | --- |
O/G |
O/G |
G |
G |
| Orchestrated Tactical IW | --- |
O/G |
O/G |
G |
G |
| Major Strategic Disruption of U.S. | --- |
--- |
--- |
G |
G |
O = Owner Responsibility
O/G = Owner Responsibility to Secure, Government surveillance
G = Government responsibility to surveil and secure
Exhibit 6-12-6. Possible IW Target Protection Responsibilities
This exhibit provides another view of how the government and private-sector roles might be defined. It also provides the Task Force view of how target protection responsibilities might be assigned. The exhibit is not intended to be authoritative, but to provide a construct for discussion of the roles of the government and the private sector.
Some areas are exclusively the responsibility of the owner, while others are exclusively the responsibility of government. It is in the areas of shared responsibility between the owner and the government where much work must be done to define levels of responsibility.
Resources must be provided if a viable defensive information warfare capability is to be achieved. The need has been recognized in part since an INFOSEC special budget issue has been submitted each of the past 3 years. The Task Force has developed a rough estimate of the resources required to get started. The Department must make a detailed estimate. The resource estimates are for resources in addition to those reflected in the proposed FY 97 budget, so some reprogramming actions will be required for FY 97.
The Task Force recommends that the ASD(C3I) develop a detailed plan of action to implement the recommendations and a detailed estimate of the resource required.
INFOSEC "special budget issue written past 3 years Rough "get started" estimates provided detailed estimates required Requires - Reprogramming FY97 ACTION: - Develop a plan and associated budget beginning in FY 97 to obtain
|
Exhibit 6-13-1. Provide the Resources
Exhibit 6-13-2 shows the estimated resources to implement the key recommendations. These are the very rough estimated resources to implement the key recommendations. The Task Force reviewed all of the individual recommendations categorized under the key recommendations and estimated to $5 million granularity what the implementation costs might be. The figures are the totals of the individual recommendations for each key recommendation. These resources are in addition to the current Information Systems Security Program and other distributed information security costs which in the aggregate total about $1.6 billion annually. The Department should perform a more detailed cost estimate.
| Major Recommendations | FY 97 | FY 98 | FY 99 | FY 00 | FY 01 | Totals |
| 1. Designate IW focal point/staff | 5 | 5 | 5 | 5 | 5 | 25 |
| 2. Organize for IW-D | 150 | 225 | 215 | 185 | 180 | 965 |
| a. I&W/TA Center | 45 | 60 | 60 | 35 | 30 | 230 |
| b. IW-D Operations Center | 35 | 60 | 60 | 60 | 60 | 275 |
| c.Planning & Coordination Ctr | 5 | 10 | 10 | 10 | 10 | 45 |
| d. Joint Arch/Design Office | 25 | 45 | 55 | 50 | 50 | 240 |
| e. Red Team & Ind. Assessments | 40 | 50 | 50 | 50 | 50 | 240 |
| 3. Increase Awareness | 35 | 65 | 85 | 135 | 135 | 455 |
| 4. Assess infra. depend's & vuln's | 45 | 45 | 0 | 0 | 0 | 90 |
| 5. Define threat cond's/responses | 0 | 0 | 0 | 0 | 0 | Existing |
| 6. Assess IW-D readiness | 10 | 5 | 0 | 0 | 0 | 15 |
| 7. "Raise the bar," ... access control | 70 | 90 | 10 | 10 | 10 | 190 |
| 8. Establish and maintain MEII | 25 | 50 | 100 | 100 | 100 | 375 |
| 9. Focus the R&D | 60 | 75 | 125 | 160 | 160 | 580 |
| 10. Staff for success | 35 | 65 | 55 | 50 | 50 | 255 |
| 11. Resolve the legal issues | 0 | 0 | 0 | 0 | 0 | Existing |
| 12. Participate fully in CIP | 0 | 0 | 0 | 0 | 0 | Existing |
| 13. Provide the resources | 0 | 0 | 0 | 0 | 0 | Existing |
| Totals | 435 | 625 | 615 | 665 | 660 | 3010 |
* Dollars in Millions
Exhibit 6-13-2. Get Started Resources
[End Section 6.0]