IW-D
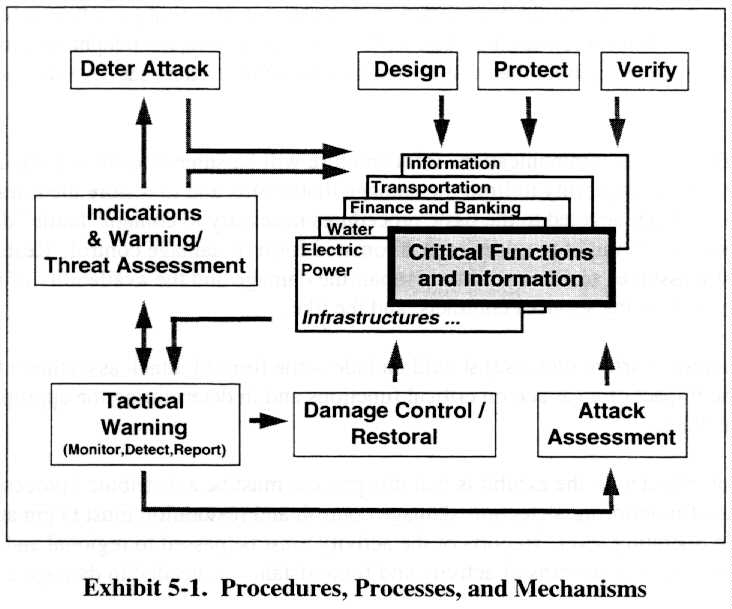
Exhibit 5- l depicts the essential procedures, processes, and mechanisms for IW-D. They are based on the defensive information warfare implementation model developed by the Information Assurance Division of the Joint Staff J6. An essential step in preparing an information warfare defense is the identification of critical national information functions and the information, information services, and infrastructures upon which these functions depend.

The first order of business is to deter information warfare attacks. This deterrence must include a national will as expressed in law and conduct, a declaratory policy on consequences of an information warfare attack against the United States, and an indication of the resiliency of the information infrastructure to survive an attack.
The most immediate need is to provide some form of protection. This protection might include physically isolating information, providing some form of access control and authentication of personnel performing critical functions or accessing information, or encryption of the information. As time permits, the information infrastructure supporting critical functions should be designed for utility, resiliency, repairability, and security. An equally important function is to verify through independent assessments that the design is being followed, that protective measures are being implemented where appropriate, and that the information warfare (defense) readiness posture is as reported.
As suggested in the Task Force observations, the importance of intelligence support to information warfare (defense) cannot be overemphasized. This support must include strategic indications and warning of potential information warfare attack, timely and accurate threat assessments, and current intelligence support in the event of an information warfare attack.
The essence of tactical warning is monitoring, detection of incidents, and reporting of the incidents. Monitoring and detection of infrastructure disruptions, intrusions, and attacks are also an integral part of the information warfare (defense) process. Providing an effective monitoring and detection capability will require some policy initiatives, some legal clarification, and an ambitious research and development program, all of which will be addressed later in the report. All intrusions and incidents should be reported so that patterns of activity can be established to aid in strategic indications and warning. The FCC requirement to report telephone outages of specified duration affecting more than a specified number of customers serves as a model in this regard.
It is probable that the telecommunications infrastructure will be subject to some form of attack. We should have some capability to limit the damage that results and to restore the infrastructure. Little research has been devoted to the basic procedures necessary to contain "battle" damage, let alone to the tools which might provide some automated form of damage control. Restoration of the infrastructure assumes some capability to repair the damage and the availability of resources such as personnel, standby services contracts, and the like.
Finally, information warfare (defense) should include some form of attack assessment to aid in determining the impact of an attack on critical functions and in determining the appropriate response to an attack.
A key point not reflected in the exhibit is that this process must be a distributed process. The basic functions of monitoring, detection, damage control, and restoration must begin at the lowest possible operating level. Reports of the activity must be passed to regional and DoD-level organizations to establish patterns of activity and for assistance as needed in damage control and restoration.
We will use the following strategy to achieve this capability for the Defense
Information Infrastructure:
[End Section 5.0]